The following data classification model is based on the guidelines from NIST SP 800-60 Guide for Mapping Types of Information and Information Systems to Security Categories and provides an overview of the types of data that is owned by Simmons categorized by the potential business risk.
Restricted
Data is classified as Restricted when the unauthorized disclosure or destruction of that data could cause a significant risk to the organization’s reputation, resources, services, individuals, or its affiliates, and as such, the highest level of security controls will be applied to this data. Restricted data is often protected by state or federal privacy regulations (e.g. HIPAA, GLBA) and/or confidentiality agreements. Simmons Information Security Policy defines sensitive information as an individual’s name, address, or telephone number combined with any of the following:
- Social security number or taxpayer ID number
- Financial account, credit or debit card number
- Financial/salary data
- Driver’s license number
- Date of birth
- Medical or health information protected under state or federal law (e.g. HIPAA)
- Access codes, security codes or passwords that would permit access to sensitive information
Additional examples of restricted data include private encryption keys and student loan application data.
Private
Data is classified as private when the unauthorized disclosure or destruction of that data could cause a high risk to the organization’s reputation, resources, services or individuals. Examples of private information would include: student data protected under state or federal law (e.g. FERPA), merchant IDs, risk & information security assessments, library circulation records, attorney-client data, donor information, networking, critical infrastructure plans or diagrams, tokens/passcodes.
Internal Use
Data is classified as Internal Use when the unauthorized disclosure or destruction of that data could cause a moderate risk to the organization’s reputation, resources, or services. Most data that is used to conduct business operations or transmitted between departments would be considered Internal Use. Examples of internal use information would include contracts, software license keys, nonpublic network addresses, business continuity plans, copyright/patent/trademark information, home address, emergency contact information.
Public
Data that is typically publicly accessible, requires minimal security controls and poses little or no risk to the organization’s reputation, resources, services, or individuals.
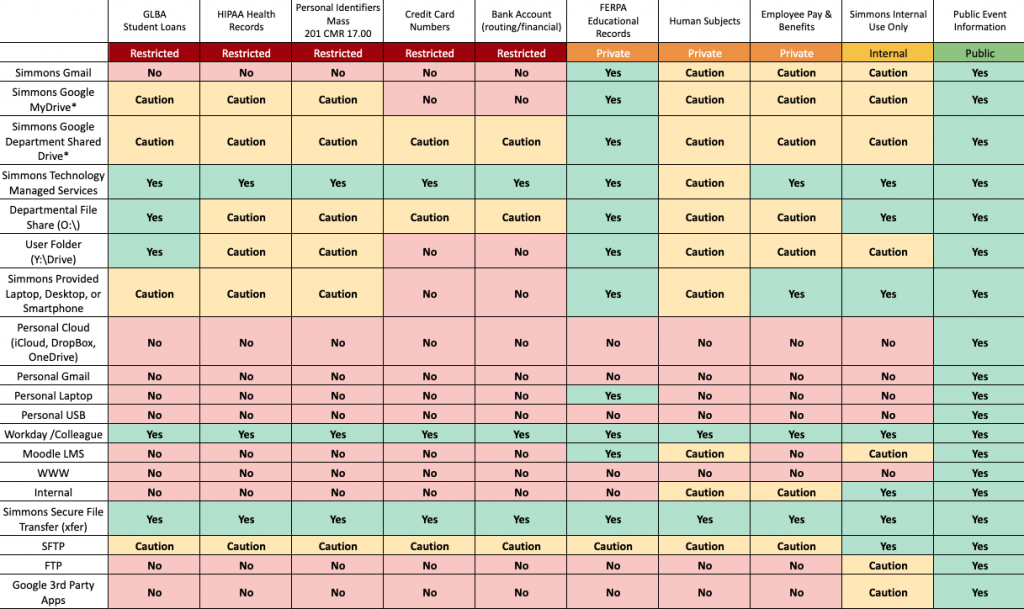
The following matrices depict the appropriate storage and transmission methods based on the data classification model and will be used as a general guideline for “what data can be stored where”. These storage and transmission practices conform with the Mass 201 CMR 17.03(2)(c).
● “Yes” – Use Permitted – No technical, policy, or contractual issues exist that prohibit use of this data type with this service. You may send, store or share the regulated data type with this service if the data owner(s) and your department/unit policies permit you to do so.
● “Caution” – Use of this service with the regulated data type is acceptable with caution and with necessary approval where required. Take special care when using the listed method for storage or transmission of data, paying particular attention to who the data is shared with and how much data is present. For example, do not send to large email lists or to “Reply All’ to large email lists.
● “No” – Use Prohibited – Use of this service with the regulated data type is prohibited. Do not use this service to send, store or share the regulated data type.
FY2021 Update
Simmons has expanded the rules that apply to storage of sensitive information on Google services to include both MyDrive (individual) and SharedDrives (department). Due to the nature of cloud-based storage, extra caution must be applied to documents stored in these locations. In addition to the cautionary notes above, the following additional policies will be enforced:
To assure data loss prevention, the following permissions and policies are to be enforced:
- Documents containing Personally Identifiable Information or Financial Data, classified as Restricted, defined by 201 CMR 17.00, may not be shared from an individual’s MyDrive or from the Department Shared Drive to any parties both internal or external to Simmons University.
- Files that are suspected of containing sensitive information may have sharing automatically revoked and may display additional warnings when being accessed, modified, or shared.
- Permissions for Shared Drive access will be managed by Simmons Technology. Upon creation, the following share permissions for Shared Drives will be applied, by default:
- Sharing with outside Simmons is disabled.
- Sharing with non-members is disabled.
- Download, copy, and print is enabled.
- Data Owners must be defined for all Department Shared Drives. Data Owners are responsible for the following:
- Requesting/approving access to Shared Drive folders
- Periodically reviewing who has access
- Requesting access be revoked for people who no longer work with your team.
- Auditing of sensitive information contained in Department Shared Drives
- Modifications of the default access permissions for these resources must be explicitly authorized by the Shared Drive Data Owner and Simmons Information Security Officer.
Additional sharing permissions that may be applied to provide additional control over designated Shared Drives:- Sharing with outside Simmons may be enabled.
- Sharing with non-members may be enabled.
- Download, copy, and print may be disabled.
- The use of 3rd Party Apps and Add-Ons must be strictly monitored for potential data access. Authorizations that request the ability to Read All Google Drive Data will be automatically classified with a minimum risk score of Medium-High, and will be subject to further security auditing and potential revocation.
Provided the storage location adheres to security guidelines included in any contracts or terms of use and that the use of these storage locations is not otherwise prohibited. Sharing with outside Simmons and non-members is to be disabled by default; modifications to default access permissions must be explicitly authorized by the data owner and Simmons Information Security Officer. Storage and transmission of Human Subjects Research data is subject to additional authorization and protocols as defined by Simmons Institutional Review Board (IRB).
Updated 04/29/2020
Approved 08/17/2020
